Design Hub configuration guide
Design Hub is a NodeJS based application for molecule design and idea management. It includes an HTTP and WebSocket server to serve multiple clients running the embedded web application.
All configuration is performed on the server, this document describes the available options.
- Configuration
- Setting up local authentication
- Setting up LDAP authentication
- Setting up SAML authentication
- Setting up OpenID Connect authentication
- Marvin JS configuration
- Groups, roles and permissions
- Structure search advanced configuration
Configuration
This application requires a JSON configuration file to be passed as a command line argument. The configuration file holds all the key settings regarding database connection, networking, security, persistence, plugins and more.
The minimum configuration requires database details, JChem Microservices details, a license and a port to be specified, but a more general sample of typical options is below. Note that some values point to files or other services. These should be changed to match your environment - of course you can store your Chemaxon license files or Design Hub plugins anywhere. See below in the spreadsheet for your full list of options:
sample for config.json:
{
"databaseHost": "db",
"databasePort": 5432,
"databaseName": "designhub",
"databaseUser": "designhubuser",
"databasePassword": "CHANGETHIS",
"secretKey": "CHANGETHIS",
"authentication": {
"internal": {
"type": "local",
"label": "Testing domain",
"accounts": [{
"username": "demo",
"password": "demo"
}]
}
},
"jchemMicroServices": "http://jms-gateway:8080/",
"mjsService": "http://mjs-service:8080/"
}Below you can find a detailed description for each option:
{warning} Note: From version 25.1.3. database connections are forced to use SSL by default.
{info} Note: All relative paths are resolved against the location of
config.json.
Database configuration
| Parameter name (environment variable) | Type | Required | Description |
|---|---|---|---|
databaseHostML_DATABASE_HOST |
string | yes | Hostname of the PostgreSQL database to connect to. |
databasePortML_DATABASE_PORT |
string | no | Port of the PostgreSQL database to connect to. Default: 5432 |
databaseNameML_DATABASE_NAME |
string | yes | Name of the database to connect to. |
databaseUserML_DATABASE_USER |
string | no | Username to authenticate with the database. |
databasePasswordML_DATABASE_PASSWORD |
string | no | Password to authenticate with the database. |
databaseSslML_DATABASE_SSL |
boolean | no | Controls if database connections are forced to use SSL, value is true by default. Setting this to false is strongly discouraged. |
databaseSslRejectUnauthorizedML_DATABASE_SSL_REJECT_UNAUTHORIZED |
boolean | no | Controls if database SSL connections must validate server certificate, value is true by default. Setting this to false is strongly discouraged. |
databaseRootCertML_DATABASE_ROOT_CERT |
string | no | Path to database root SSL certificate file. If this is set the database connections use SSL with certificate validation. |
databaseVersionML_DATABASE_VERSION |
string | no | PostgreSQL dialect version to use in the Design Hub SQL client. Use this when connect to different flavors of PSQL, e.g. Enterprise DB. |
databaseMinPoolSizeML_DATABASE_MIN_POOL_SIZE |
number | no | PostgreSQL database connection's minimum pool size. Default: 2 |
databaseMaxPoolSizeML_DATABASE_MAX_POOL_SIZE |
number | no | PostgreSQL database connection's maximum pool size. Default: 10 |
fileStoreML_FILE_STORE |
string | yes | Path to the folder where files uploaded by users can be saved. The folder needs to be writable to the main NodeJS process running under uid=2584, gid=1597.Default: /filestore which corresponds to a volume declared by default in the Design Hub docker image. |
filestoreImplementationML_FILESTORE_IMPLEMENTATION |
string | no | Controls what backend to use when users upload files. The default solution uses a filesystem backend, using generated filenames. If file system access is a burden, then Design Hub's database can be used. For a cloud solution, an AWS S3 bucket can be configured to persist files. To use the latter option, the filestoreS3BucketName option must be set. Maximum file size is 100 MB for database and 1000 MB for disk and S3.Default: diskValues: disk, database or S3 |
filestoreS3BucketNameML_FILESTORE_S3_BUCKET_NAME |
string | see description | Defines the name of an AWS S3 bucket to save files to when users initiate uploads. The Design Hub process must have permissions to execute the getBucketAcl, upload, getObject, deleteObject methods, and credentials must be supplied using a method natively supported by the AWS SDK. For more details read its documentation.Required: yes when filestoreImplementation is set to S3 |
Chemistry web services configuration
| Parameter name (environment variable) | Type | Required | Description |
|---|---|---|---|
jchemMicroServicesML_JCHEM_MICRO_SERVICES |
string | see description | URL to JChem Microservices gateway module without the rest-v1/ ending.Required: either jchemMicroservices or all of jmsIo, jmsDb, jmsStructureManipulation are required |
jmsIoML_JMS_IO |
string | see description | URL to the JChem Microservices IO module without the rest-v1/ ending. Use this if JMS IO is deployed without a gateway service, for example as a standalone service.Required: either jchemMicroservices or all of jmsIo, jmsDb, jmsStructureManipulation are required |
jmsDbML_JMS_DB |
string | see description | URL to the JChem Microservices DB module without the rest-v1/ ending. Use this if JMS DB is deployed without a gateway service, for example as a standalone service.Required: either jchemMicroservices or all of jmsIo, jmsDb, jmsStructureManipulation are required |
jmsStructureManipulationML_JMS_STRUCURE_MANIPULATION |
string | see description | URL to the JChem Microservices Structure Manipulation module without the rest-v1/ ending. Use this if JMS Structure Manipulation is deployed without a gateway service, for example as a standalone service.Required: either jchemMicroservices or all of jmsIo, jmsDb, jmsStructureManipulation are required |
jmsMarkushML_JMS_MARKUSH |
string | see description | URL to the JChem Microservices Markush Enumeration module without the rest-v1/ ending. Use this if JMS Markush Enumeration is deployed without a gateway service, for example as a standalone service. This module is needed for the contentAnalyzers features to work.Required: yes if contentAnalyzers are enabled. |
jmsReactorML_JMS_REACTOR |
string | see description | URL to the JChem Microservices Reactor module without the rest-v1/ ending. Use this if JMS Reactor is deployed without a gateway service, for example as a standalone service. This module is needed for the reactionEnumeration features to work.Required: yes if reactionEnumeration are enabled. |
jchemMicroServicesTypeName |
string | no | Configures the molecule type used to standardize chemical structures for the purposes of searches and virtual registration in the JChem Microservices DB module. Must be one of the available types already configured. For details, please see DB Web Services documentation. Default: sample |
mjsServiceML_MJS_SERVICE |
string | yes | URL to the Marvin JS web service module without the rest-v1/ ending. For details, please see Marvin JS Web Service documentation. |
Plugin configuration
| Parameter name (environment variable) | Type | Required | Description |
|---|---|---|---|
servicesDirectoryML_SERVICES_DIRECTORY |
string or array of strings | no | Path to the folder(s) of the docker container where NodeJS plugins are stored. The /services folder is declared as a docker volume, so it expected a deployment will mount a folder to this volume. See Volumes. Changing this folder is not recommended. Default: /services |
remoteServices |
array of strings | no | List of URLs to load plugins implementing the Design Hub HTTP Plugin API specification. For further details and examples, check the relevant developer guides. |
License configuration
| Parameter name (environment variable) | Type | Required | Description |
|---|---|---|---|
licenseML_LICENSECHEMAXON_LICENSE_URL |
string or array of strings | yes | Path to the license file(s) provided by Chemaxon for this application, accepting wildcards like *.cxl. |
Networking configuration
| Parameter name (environment variable) | Type | Required | Description |
|---|---|---|---|
tls |
object | no | HTTPS server options in key-value pair form. All options of the NodeJS TLS module are supported, but the most typical 4 options are highlighted below: key, cert, ca, pfx. For more configuration options and details see the official module description . |
tls.key |
string | no | Path to the private key of the server in PEM format. |
tls.cert |
string | no | Path to the certificate key of the server in PEM format. |
tls.ca |
string | no | Path to the trusted certificates in PEM format. If this is omitted, several well known "root" CAs will be used, like VeriSign. These are used to authorize connections. |
tls.pfx |
string | no | Path to the bundle of private key, certificate and CA certs of the server in PFX or PKCS12 format. Mutually exclusive with tls's key, cert and ca options. |
hostnameML_HOSTNAME |
string | see description | Hostname of the server. Needed only for single sign-on authentication, where a service callback needs to registered. Required: if SAML authentication is configured |
portML_PORT |
number | yes | The HTTP port you want the application to bind to. In Docker environments this is configured to an exposed port, therefore modifying this shouldn't necessary under normal circumstances. Default: 8888 |
allowCrossOriginUploadsML_ALLOW_CROSS_ORIGIN_UPLOADS |
boolean | no | Enable CORS on the /upload/api endpoint of the (REST API).Default: false |
Logging
| Parameter name (environment variable) | Type | Required | Description |
|---|---|---|---|
ML_LOG_LEVEL |
string | no | Configures which application module is started at elevated or reduced log levels. For each module, ERROR, WARN, INFO or DEBUG log levels are available. The default log level is info for all modules.Syntax: global_log_level [log_level=module_name] [log_level=module_name] ...i.e. a space separated list of definitions, starting with a global level, followed by = separation between a log level and a module name. For a list of module names, it is recommended to always consult with Chemaxon technical support as module names refer to application modules subject to constant changes as the application is developed. This configuration option is only available as an environment variable.Default: info. Example: info\ warn=authentication |
ML_AUDITLOG_LEVEL |
string | no | Configures the log level of the application's audit log. error, warn, info or debug log levels are available. This configuration option is only available as an environment variable.Default: info. |
ML_LOG_FORMAT |
string | no | Configures the string format of the log messages. flat is a traditional space separated output. json packs each log message into a separate valid JSON object with the following (easy to filter) attributes: "eventTime", "level", "label", "recordType", "message". This configuration option is only available as an environment variable.Default: flat. |
ML_LOG_TRANSPORT |
string | no | Configures which additional transports to send logged messages beyond standard output. This configuration option is only available as an environment variable. Available options: file and gelf |
ML_LOG_FILEPATH |
string | no | Configures the local filepath to write log messages to if ML_LOG_TRANSPORT is set to file. Example: /var/log/designhub.log. |
ML_LOG_GELF_HOST |
string | no | Hostname of the Graylog Extended Log Format (GELF) compatible server, like Graylog. Only used if ML_LOG_TRANSPORT is gelf. |
ML_LOG_GELF_PORT |
number | no | Port of the graylog stream to send messages. Used only if ML_LOG_TRANSPORT is gelf. This configuration option is only available as an environment variable.Default: 12201 |
ML_LOG_GELF_PROTOCOL |
string | no | Protocol of the graylog stream to send messages. This configuration option is only available as an environment variable. Default: udp |
Security configuration
| Parameter name (environment variable) | Type | Required | Description |
|---|---|---|---|
secretKeyML_SECRET_KEY |
string | yes | Private key used to encrypt the contents of session cookies. This string should be known only to the administrator of the server and should never be reused. |
authentication |
object | yes | The available identity providers users can authenticate with, in key-value pair form. Key: identifier or name of the domain, containing only lowercase letters, numbers and -, i.e: [a-z0-9-]+Value: object containing the settings for the domain and protocol specific settings. Each option must have the following 2 attributes, but may specify further options: label and type. The default user object attribute mapping can be overridden by setting userNameAttribute, displayNameAttribute and groupAttribute.Provider specific options are described below in separate sections: LDAP, SAML, local, OpenID Connect. |
authentication.<domain>.label |
string | yes | Human readable name of the domain. |
authentication.<domain>.type |
string | see description | "ldap", "saml", "openId", "local". Further, provider specific options are described below in separate sections` |
oidcTimeout |
number | no | Configures global timeout for the HTTP requests of openId type authentication module.Default: 5000 |
adminUsernameML_ADMIN_USERNAME |
string | no | Username used to authenticate in the admin area. For details on access see the admin guide. |
adminPasswordML_ADMIN_PASSWORD |
string | no | Password used to authenticate in the admin area. Consider loading this password from a file with limited read permissions to prevent other users of the operating system from seeing the value of this sensitive setting. |
hideDomainsOnLoginScreen |
boolean | no | Hides the domain picklist from the login page. When set to true, generated login URLs are printed on STDOUT, one for each authentication domain.Default: false |
GUI configuration
| Parameter name (environment variable) | Type | Required | Description |
|---|---|---|---|
themeOverridesML_THEME_OVERRIDES |
string | no | Path to a CSS file that adds or changes styles used in the Design Hub theme. Default: no custom CSS file |
marvinjs |
object | no | Configure Marvin JS’s display options and services (API reference). For details, find the Marvin JS configuration section below. Example: "marvinjs": { |
systemHelp |
array of objects | no | Adds additional links to the help menu available to users. Use this to provide more options to get technical support for on-premises deployments or related to custom plugin backends |
systemHelp[*].label |
string | no | Human-friendly label of an additional help item |
systemHelp[*].url |
string | no | Absolute URL (starting with https://) to the help item |
compoundButtons |
array of objects | no | Configures clickable links for compounds pointing to external resources |
compoundButtons[*].label |
string | yes | Human friendly label of the button, e.g. ELN |
compoundButtons[*].link |
string | yes | A URL with variable names surrounded by % signs that are interpolated as the user is clicking on them. |
commentFinalMinutesML_COMMENT_FINAL_MINUTES |
number | no | Configures the interval while comments can be modified or deleted by their owner. Configuration value is given in minutes. Default: 10 (10 minutes) |
compoundFields |
array of objects | no | Configures "Additional Fields", i.e. custom editable text fields for compounds |
compoundFields[*].name |
string | yes | Unique internal identifier of this field |
compoundFields[*].label |
string | yes | Human-friendly label of this field |
compoundFields[*].type |
string | no | Data type of this field. Values: text, textEnum, numeric, url. Default: text |
compoundFields[*].group |
string | no | Group used for permission control of the field access. Supported values are group1, group2, group3 with corresponding permissions ACCESS_COMPOUND_FIELDS_GROUP_1, ACCESS_COMPOUND_FIELDS_GROUP_2, ACCESS_COMPOUND_FIELDS_GROUP_3 Default: group1 |
compoundFields[*].values |
array of strings | no | When defined, the field will be displayed as a combobox/dropdown with these values as choices. When missing, the field is displayed as a text input field. |
compoundFields[*].required |
boolean | no | Turns the field into mandatory field, with an asterisk and red underline if left empty. |
compoundFields[*].pattern |
Regexp | no | A regular expression that is used to validate the input, e.g. \d+ can be used to allow only numbers. |
Workflow configuration
| Parameter name (environment variable) | Type | Required | Description |
|---|---|---|---|
registry |
object | no | Configures how Design Hub should generate unique virtual IDs to compounds when they are shared (i.e. transitioned from private to public visibility). |
registry.externalCheckStop |
string | no | Configures how long after sharing a compound should be checked on a daily basis in a real compound registry. All compounds in a workflow status of shared are checked every day.Syntax: <number><period> where period can be one of: d (day), w (week), m (month), y (year).Default: 3m |
registry.idPrefix |
string | no | Configures what string to prefix numeric ids with. For example with a value of VXN the id of compound 123456 will be VXN123456.Default: CPD |
registry.idSeparator |
string | no | Configures what string to use - if any - as a separator between the idPrefix and the numeric id portion. For example with a value of - the id of compound 123456 will be CPD-123456.Default: (empty string) |
registry.idStart |
number | no | Configures what number to add to sequential ids generated during compound sharing. For example with a value of 500000 and the id of compound 123456 will be CPD623456.Default: 0 |
registry.idPadding |
number | no | Configures how many decimal places to pad on the left with 0 characters. For example with a value of 9, the id of compound 123456 will be CPD000123456.Default: 0 |
registry.excludeSubstancesFromChecks |
boolean | no | when enabled, compounds with a substance ID are ignored from periodic checks regardless of their status. This allows tracking the progress made during re-synthesis or any follow-up batches for a compound already registered once as a substance. |
registry.matchLogicDeprecated |
string | no | Configures match mode between 1 virtual compound and substances. automatic allows matching exactly 1 substance, while multi allows matching to multiple substances over a period of time. In case of multiple matches, the compound's author is prompted to select matches if the requiresApproval property was not set to false. With the requiresApproval property set to false, Design Hub automically assings id as susbstance-id to the virtual copmpound. Values: automatic, multi.Default: automatic if the registry plugin exposes only the getID function, multi otherwise. |
registry.singleMatchWait |
string | no | Sets the time period after which a single substance match is automatically approved. Syntax: <number><period> where period can be one of: d (day), w (week), m (month), y (year).Default: 1w. Value should be larger than 1d as the system makes no guarantee a virtual compound will be checked more than once a day. |
registry.copyCSTFields |
array of strings | no | List of compoundFields names to be updated with data of Substance matches during approval. See registry plugins. |
registry.checkCSTFields |
array of strings | no | List of compoundFields names whose value is to be provided during getMatches call in registry plugins. See registry plugins. |
hypothesisTitleGeneration |
object | no | Configures how Design Hub should automatically generate hypothesis identifier for new hypotheses. When configured, hypothesis titles are generated using a prefix, sequential numbering, and optional project-specific starting values append free text title to it |
hypothesisTitleGeneration.prefix |
string | no | Prefix string to prepend to hypothesis titles. For example, with a value of "HYP" and sequence 00123, the generated title will be HYP00123. |
hypothesisTitleGeneration.sequenceDigits |
number | no | Number of digits to use for the sequence number with zero-padding on the left. For example, with a value of 5, sequence numbers will be formatted as 00001, 00002, etc.Default: 5 |
hypothesisTitleGeneration.sequenceStart |
object | no | Project-specific starting sequence numbers in key-value pair form. Key is the project name, value is the starting sequence number for hypotheses in that project. For example, {"Alpha": 25, "Beta": 100} will start numbering at 25 for "Alpha" and 100 for "Beta". Projects not listed will start at 1.Default: {} |
schedulerPlan |
string | no | Configures the frequency and batching of registry plugin calls. normal processes 50 compounds every 5 minutes on weekdays. continuous processes 1 compound every 5 seconds every day. Default: normal. |
Example configuration for hypothesis title generation:
{
...
"hypothesisTitleGeneration": {
"prefix": "HYP",
"sequenceDigits": 5,
"sequenceStart": {
"Alpha": 25,
"Beta": 100
}
},
...
}With this configuration:
- New hypotheses in project "Alpha" will be titled
HYP00025,HYP00026,HYP00027, etc. - New hypotheses in project "Beta" will be titled
HYP00100,HYP00101,HYP00102, etc. - New hypotheses in other projects will start from
HYP00001
Performance configuration
| Parameter name (environment variable) | Type | Required | Description |
|---|---|---|---|
limitPublicCompoundsListSize |
number | no | Configures the maximum size of list provided via API /api/compounds/public Default: 1000 |
limitStructureSearch |
number | no | Defines the maximum hit count of the first chemical search for all chemical search types. Default: 10000. |
limitFilterToIds |
number | no | Defines the maximum number of compound ids provided to refine substructure searches. Default: 100000 |
limitFilteredStructureSearch |
number | no | Defines the maximum hit count of refined substructure searches. Default: 10000 |
structureSearchCacheTTLSeconds |
number | no | Configures the cache duration for al chemical searches in seconds. Default: 30 |
structureSearchCacheMaxSize |
number | no | Configures the cache size for all chemical searches. Default: 1000 |
calcDataColumnLimitML_CALC_DATA_COLUMN_LIMIT |
number | no | Configures the maximum number of columns/fields the project data and design set spreadsheets can query from the database at a time. Default: 200 |
calcDataColumnSampleSizeML_CALC_DATA_COLUMN_SAMPLE_SIZE |
number | no | Configures the number of compounds to scan per spreadsheet when querying columns/fields for spreadsheets or shared compounds plugin. (Recent compounds considered first based on modification date) Default: 500 |
disableMetadataCacheML_DISABLE_METADATA_CACHE |
any | no | Metadata (columns/fields) is cached for 30 seconds by default, it can be disabled by defining this parameter. |
importMaxFileSizeInMb |
number | no | Configures the maxium file size uploaded for import. The unit is megabytes. Default: 15. |
importPrivateMaxStructureCount |
number | no | Maximum number of structures that can be imported in a single go into a private design set. Default: 1000000 |
importPublicMaxStructureCount |
number | no | Maximum number of structures that can be imported in a single go into a public design set. Default: 1000 |
markushEnumerationTimeout |
number | no | Timeout on requests sent to the markush enumeration service. Default: 60000 |
saveAllPrivateComponentsMaxCount |
number | no | Maximum number of enumerated components that can be imported in a single go into a private design set. Default: 10000 |
saveAllPublicComponentsMaxCount |
number | no | Maximum number of enumerated components that can be imported in a single go into a public design set. Default: 100 |
extRegCheckMaxConcurrency |
number | no | Number of maximum concurrent calls to external registry. Default: 1. |
extRegCheckLocal |
boolean | no | Controls cocurrency limit scope of external registry. If false, the limit is applied globally in a Design Hub instance. Default: false. |
cmpdSubmissionRestMaxConcurrency |
number | no | Number of maximum concurrent calls to internal registry. Default: 1. |
cmpdSubmissionRestLocal |
boolean | no | Controls cocurrency limit scope of internal registry. If false, the limit is applied globally in a Design Hub instance. Default: true. |
uploadCache |
number | no | Configures the expiry interval of chemical structure files uploaded using the REST API. Configuration value is given in milliseconds. Default: 720000 (2 hours) |
DH_JMSIO_MAX_CONCURRENCY |
number | no | Controls the global maximum number of parallel web service calls to JChem Microservices IO module. Default: 20. |
cmpdImageGenerationTimeout |
number | no | Default: 1500. |
importProcessBatchSize |
number | no | Number of records to process in a batch of import tasks. Default: 100. |
importSchedulerPlan |
string | no | Frequency of processing of automatically imported records. Default: normal. Values: normal (every 5 minutes), crazy (every minute), or dontTryThisAtHome (every second). |
Setting up local authentication
Design Hub supports a very simple local authentication intended for personal testing or evaluation purposes. This enables all features depending on tracking users and storing profiles, without having to setup identity provider connections. Accounts are read from a list specified in config.json. Below you can find a sample:
{
"port": 443,
"hostname": "example.com",
"tls": {
"key": "/config/certs/example-com-key.pem",
"cert": "/config/certs/example-com-cert.pem"
},
"secretKey": "lalilulelo",
"authentication": {
"test": {
"type": "local",
"label": "Test Ltd",
"accounts": [
{"username": "demo", "password": "demo"},
{"username": "demo2", "password": "demo2"}
]
}
}
}Setting up LDAP authentication
The application supports LDAP and LDAPS authentication, which works with Active Directory as well. The most common configuration options are supported. Below you can find a sample configuration and a full list of options:
{
"port": 443,
"hostname": "example.com",
"tls": {
"key": "/config/certs/example-com-key.pem",
"cert": "/config/certs/example-com-cert.pem"
},
"secretKey": "lalilulelo",
"authentication": {
"corporate": {
"type": "ldap",
"label": "ACME Inc",
"url": "ldaps://ipa.acme.com:636",
"bindDn": "uid=serviceaccount,cn=accounts,dc=acme",
"bindCredentials": "BF95KPnVD9FxyGPh",
"searchBase": "cn=accounts,dc=acme",
"searchFilter": "(uid={{username}})",
"groupSearchBase": "dc=acme",
"groupSearchFilter": "(member={{dn}})",
"groupAttribute": ["cn"]
}
}
}LDAP configuration options
| Name | Type | Description |
|---|---|---|
url |
string | full URL of LDAP server, including protocol and port, e.g: ldaps://ldap.company.tld:636/ |
bindDn |
string | DN of user permitted to search the LDAP server within the defined search base |
bindCredentials |
string | password for bindDn |
searchBase |
string | part of the directory to search in for the user, e.g: cn=users,dc=company |
searchFilter |
string | search filter that should match the user with either 1 or 0 entries. Use literal {{username}} to add the given username to the search, e.g: (uid={{username}}) |
firstName |
string | LDAP attribute that holds the display name of the user |
searchAttributes |
array of strings | Optional. Names of attributes to fetch from the LDAP server, e.g: ['displayName', 'mail']. 'mail' is a required element for functionality relying on users' email addresses (such as notifications about new comments). |
groupSearchBase |
string | part of the directory to search in for the available groups, e.g. dc=groups,dc=company |
groupSearchFilter |
string | search filter that should match the groups of a user. Use literal {{attribute}} to add an attribute to the search, e.g: (member={{dn}}) |
groupAttribute |
array of strings | name of the attribute to use as Design Hub group names, e.g.: ["cn"] |
userNameAttribute |
string | name of the attribute to use as Design Hub's unique user name. Default: "dn" |
displayNameAttrs |
array of strings | name of the attributes to concatenate a Display Name from, e.g.: ["firstName", "lastName"] |
{info} Note: All options described in the base library documentation are supported with further examples and descriptions given at: node-ldapauth
Setting up SAML authentication
This application uses HTTP Redirect Binding for its AuthnRequests, and expects to receive the messages back via the HTTP POST binding.
Configuration
First, you’ll need to configure the application with a host. You can do this by setting port, and hostname. Next, it’s strongly recommended to setup HTTPS with the tls settings, to make sure any login details are only transmitted over a secure channel.
config.json:
{
"port": 443,
"hostname": "example.com",
"tls": {
"key": "/config/certs/example-com-key.pem",
"cert": "/config/certs/example-com-cert.pem"
}
}Next, add a secretKey and configure your identity provider in authentication:
config.json:
{
"port": 443,
"hostname": "example.com",
"tls": {
"key": "/config/certs/example-com-key.pem",
"cert": "/config/certs/example-com-cert.pem"
},
"secretKey": "lalilulelo",
"authentication": {
"internal": {
"type": "saml",
"label": "Example",
"entryPoint": "http://idp.example.com/oam/SSORedirect/metaAlias/apps/idp"
}
}
}Registering as Service Provider
Using the domain chosen in the authentication settings, in the above example internal, the Design Hub service can be registered in the SAML provider. To help this, a service metadata descriptor is available at the following address:
https://example.com/domains/internal/metadata
The service’s issuer / entity ID is marvin-live-app and the callback URL is generated from the tls, hostname, port and domain name options.
<?xml version="1.0"?>
<EntityDescriptor xmlns="urn:oasis:names:tc:SAML:2.0:metadata" xmlns:ds="http://www.w3.org/2000/09/xmldsig#" entityID="marvin-live-app">
<SPSSODescriptor protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol">
<KeyDescriptor/>
<NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified</NameIDFormat>
<AssertionConsumerService index="1" isDefault="true" Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://example.com/domains/internal/callback"/>
</SPSSODescriptor>
</EntityDescriptor>SAML specific parameters
| Name | Type | Description |
|---|---|---|
entryPoint |
string | URL for the identity provider. Required: yes |
cert |
string | Path to the identity provider’s certificate used to validate any SAML authorization responses. |
privateCert |
string | Path to the certificate used to sign any SAML authentication requests. |
decryptionPvk |
string | Path to the private key of the identity provider, used to decrypt any encrypted assertions that are received |
decryptionCert |
string | Path to the certificate used to attach to the service metadata. |
identifierFormat |
string | Name ID format to request from the identity provider. The use of unspecified and transient are not recomennded to enable private room usage. Default: urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress |
callbackUrlBase |
string | Alternative Design Hub server URL to use when generating metadata, and in SAML requests. Used when the application is behind a reverse proxy. |
emailAttribute |
string | The name of the attribute in the IdP assertion carrying the email of the user. In the absence of this setting the mail or email attribute are used if present or the NameID in case it is of the urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress format. |
Further options are available, please see this third-party module’s options.
Setting up OpenID Connect authentication
The application supports OpenID Connect authentication. Below you can find a sample configuration and a full list of options:
{
"port": 443,
"hostname": "example.com",
"tls": {
"key": "/config/certs/example-com-key.pem",
"cert": "/config/certs/example-com-cert.pem"
},
"secretKey": "lalilulelo",
"authentication": {
"corporate": {
"type": "openId",
"label": "ACME Inc",
"issuer": "https://myissuer.com",
"clientID": "dh-client",
"clientSecret": "password",
"callbackUrlBase": "https://example.com"
}
}
}OpenID Connect specific configuration options
| Name | Type | Description |
|---|---|---|
issuer |
string | URL of the Issuer if the issuer supports standard OIDC Discovery, or URL of the OpenID Connect metadata document. OIDC Discovery path constants are supported, e.g. "https://myissuer.com/" behave equivalent to "https://myissuer.com/.well-known/openid-configuration". |
clientID |
string | client ID generated by Issuer for this application |
clientSecret |
string | client secret generated by Issuer for this application. Optional. If clientSecret is not specified, PKCE is forced. |
pkce |
string | Code challenge method for PKCE. Valid values: plain, S256. In case of missing clientSecret S256 is the default. Optional. |
callbackUrlBase |
string | URL of the Design Hub reachable from Issuer |
scope |
string | Provided if needed for getting enough user information. Example: "openid profile email". Default: "". |
tokenAutoRefreshInterval |
number | Time interval is milliseconds between token refreshes. If omitted, refresh tokens won't be used. |
userNameAttribute |
string | Name of the attribute to use as Design Hub's unique user name. Default: "preferred_username" with a fallback to "username". |
Marvin JS configuration
This option configures Marvin JS’s display options and services (API reference). An object is passed as configuration with the following attributes:
| key | value |
|---|---|
templates |
Path to an MRV formatted template file |
webservices |
Map of webservice names and URLs matching MarvinJS's setServices() method.Default: { "clean2dws": "/rest-v1/util/convert/clean", "molconvertws": "/rest-v1/util/calculate/molExport", "reactionconvertws": "/rest-v1/util/calculate/reactionExport", "stereoinfows": "/rest-v1/util/calculate/cipStereoInfo" } |
displaySettings |
Map of display settings and values. Default: { "toolbars": "search" } |
Reference: https://marvinjs-demo.chemaxon.com/latest/jsdoc.html
Example:
section of config.json:
...
"marvinjs": {
"templates": "./templates.mrv",
"webservices": {
"clean2dws": "/rest-v1/util/convert/clean",
"molconvertws": "/rest-v1/util/calculate/molExport",
"reactionconvertws": "/rest-v1/util/calculate/reactionExport",
"stereoinfows": "/rest-v1/util/calculate/cipStereoInfo"
},
"displaySettings": {
"toolbars": "reporting"
}
}
...Groups, roles and permissions
From v20.13.0, the role based access control system can be used to assign authenticated users of the system to groups and roles/permissions can be assigned to groups.
Definings group and permissions of users
Company plugins
Design Hub's customization option - company plugins - provide scriptable interfaces to obtain the project and group membership of each user during login. This is the most versatile option to integrate with corporate resources.
See: Design Hub developer guide - company support plugins
Property of user's login information
In some cases, the user's group associations are available as an attribute of the user record. This is typically the case of ldap / Active Directory, but often it's available on JWT when using openId.
To obtain the groups of a user from the user record, please use the groupAttribute value. See
Local authentication
By adding a groups section to the domain configuration, individual groups can be added with a name (e.g. READERS or WRITERS) and a list of permissions. With local authentication, individual accounts can be assigned to a group by referencing the assigned group name on each account record.
{
...
"authentication":
"access-readonly": {
"type": "local",
"label": "Read-only authorization scheme",
"groups": {
"READERS": [
"ACCESS_HYPOTHESES",
"READ_NONASSIGNED_CONTENT",
"READ_NONASSIGNED_PROJECTS",
"JOIN_PROJECTS"
],
"WRITERS": [
"ACCESS_HYPOTHESES",
"ADD_PROJECTS",
"CREATE_CONTENT",
"WRITE_NONASSIGNED_CONTENT",
"WRITE_NONASSIGNED_PROJECTS"
"JOIN_PROJECTS"
]
},
"accounts": [
{"username": "vip", "password": "vip", "group": "VIP"},
{"username": "reader", "password": "reader", "group": "READERS"},
{"username": "writer", "password": "writer", "group": "WRITERS"}
]
}
}
...
}Defining groups on the admin interface
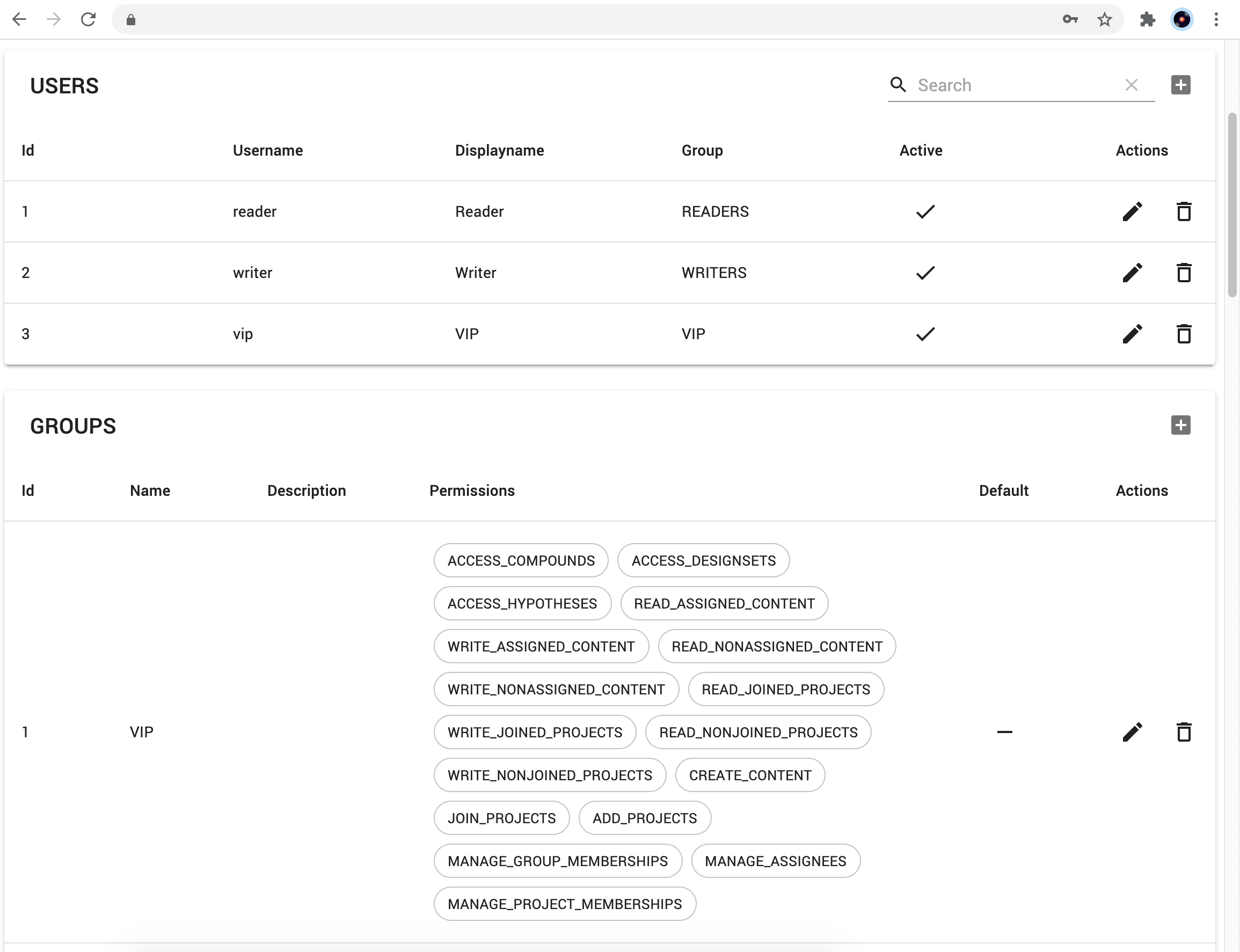
By logging in to the admin interface and selecting the appropriate domain, the list of users and groups are displayed in small tables. These can be used to check the list of groups available in the system, permissions assigned to each group, and the group membership of users. Using the buttons in the top-right corner of the groups table, new groups can be added, and using the actions for each group, further modifications can be made.
Available permissions
| Name | Description |
|---|---|
READ_ASSIGNED_PROJECTS |
Allows viewing any content in projects where the user is member, unless restricted by READ_ASSIGNED_CONTENT and READ_NONASSIGNED_CONTENT. |
WRITE_ASSIGNED_PROJECTS |
Allows viewing, modifying or deleting any content in projects where the user is member, unless restricted by WRITE_ASSIGNED_CONTENT and WRITE_NONASSIGNED_CONTENT. |
READ_NONASSIGNED_PROJECTS |
Allows viewing any content in projects where the user is not a member |
WRITE_NONASSIGNED_PROJECTS |
Allows viewing, adding, modifying or deleting content in projects where the user is not a member |
READ_ASSIGNED_CONTENT |
Allows viewing content where the user is assigned |
WRITE_ASSIGNED_CONTENT |
Allows viewing, modifying or deleting content the where user is assigned |
READ_NONASSIGNED_CONTENT |
Allows viewing content where the user is not assigned |
WRITE_NONASSIGNED_CONTENT |
Allows viewing, modifying or deleting content where the user is not assigned |
ACCESS_COMPOUNDS |
Allows viewing compounds |
ACCESS_DESIGNSETS |
Allows viewing design sets and compounds |
ACCESS_HYPOTHESES |
Allows viewing hypotheses, design sets, and compounds |
ACCESS_PROJECTS_META |
Allows viewing the list of projects and use the information in it for queries |
ADD_PROJECTS |
Allows adding projects to the system, if a company support plugin implements the necessary capability, or none are used |
JOIN_PROJECTS |
Allows adding to or deleting from the project membership of the user |
CREATE_CONTENT |
Allows creating new hypotheses, design sets and compounds |
ACCESS_REST_API |
Allows creating, revoking, viewing API tokens and making REST API requests with token based authorization |
ACCESS_TAGS |
Allows viewing, adding and removing tags. |
ACCESS_ALL_PROPERTY |
Allows access to imported data, execution of realtime plugin calculations, and viewing of the resulting outputs. |
ACCESS_VOTING |
Allows viewing and casting votes on compounds |
ACCESS_SUBSTANCE_ID |
Allows viewing, searching and exporting substance IDs of compounds. |
READ_INTERNAL_COMMENTS |
Allows viewing internal comments on content otherwise accessible to the user |
WRITE_INTERNAL_COMMENTS |
Allow making, editing and deleting internal comments on content otherwise accessible to the user |
READ_PUBLIC_COMMENTS |
Allows viewing public comments on content otherwise accessible to the user |
WRITE_PUBLIC_COMMENTS |
Allow making, editing and deleting public comments on content otherwise accessible to the user |
ACCESS_INTERNAL_FILE_ATTACHMENT |
Allows listing, downloading and upload internal and public file attachments on projects, as part of using realtime plugins, or on content otherwise accessible to the user |
ACCESS_FILE_ATTACHMENT |
Allows listing, downloading and upload public file attachments on projects, as part of using realtime plugins, or on content otherwise accessible to the user |
READ_DESCRIPTION |
Allows viewing description on content |
WRITE_DESCRIPTION |
Allows editing description on content |
ACCESS_COMPOUND_FIELDS_GROUP_1 |
Allows reading and changing values of compound fields in group 1 |
ACCESS_COMPOUND_FIELDS_GROUP_2 |
Allows reading and changing values of compound fields in group 2 |
ACCESS_COMPOUND_FIELDS_GROUP_3 |
Allows reading and changing values of compound fields in group 3 |
ACCESS_PROPERTY_GROUPS |
Allows executing and viewing selected compound properties the sources of which (realtime plugins, import plugins or by-upload import) have been configured to be access-controled by this permission |
DOMAIN_ADMIN |
Allows accessing the Design Hub admin area related to the current domain |
MODIFY_STRUCTURE |
Allows changing shared compounds on compounds where write permissions are otherwise available (see other READ/WRITE permissions above) |
CREATE_PROGRESS_REPORT |
Allows accessing the downloadable report of the Kanban board where contents are further filtered based on read permissions |
NOTE:
ACCESS_PROPERTYpermission has been removed and replaced byACCESS_ALL_PROPERTY, along with the addition of three new granular permissions:ACCESS_PROPERTY_GROUP_1,ACCESS_PROPERTY_GROUP_2, andACCESS_PROPERTY_GROUP_3. See further details under Granular permission control section.
Granular permission control
Design Hub’s admin interface provides fine-grained control over access to compound properties - whether obtained through realtime plugins, imported manually or automatically allowing administrators to tailor data visibility based on user roles. This ensures that each user group can only access the compound properties relevant to their work, enhancing both clarity and security.
The legacy ACCESS_PROPERTY permission has been deprecated and replaced with a more flexible model:
-
ACCESS_ALL_PROPERTY: A master permission that grants access to all compound properties and imported data, regardless of their assigned group. It mirrors the behavior of the oldACCESS_PROPERTYbut within the new granular framework. -
ACCESS_PROPERTY_GROUP_1,ACCESS_PROPERTY_GROUP_2,ACCESS_PROPERTY_GROUP_3: These granular permissions control access to compound properties assigned to them.
User Group Configuration
For each user group in Design Hub, administrators can configure which ACCESS_PROPERTY_GROUPS are enabled. These settings determine whether a compound property is visible and accessible in the UI for that group.
By default, regular users have access to all compound properties via the ACCESS_ALL_PROPERTY permission, unless otherwise restricted.
Plugin categories and Access Property Groups
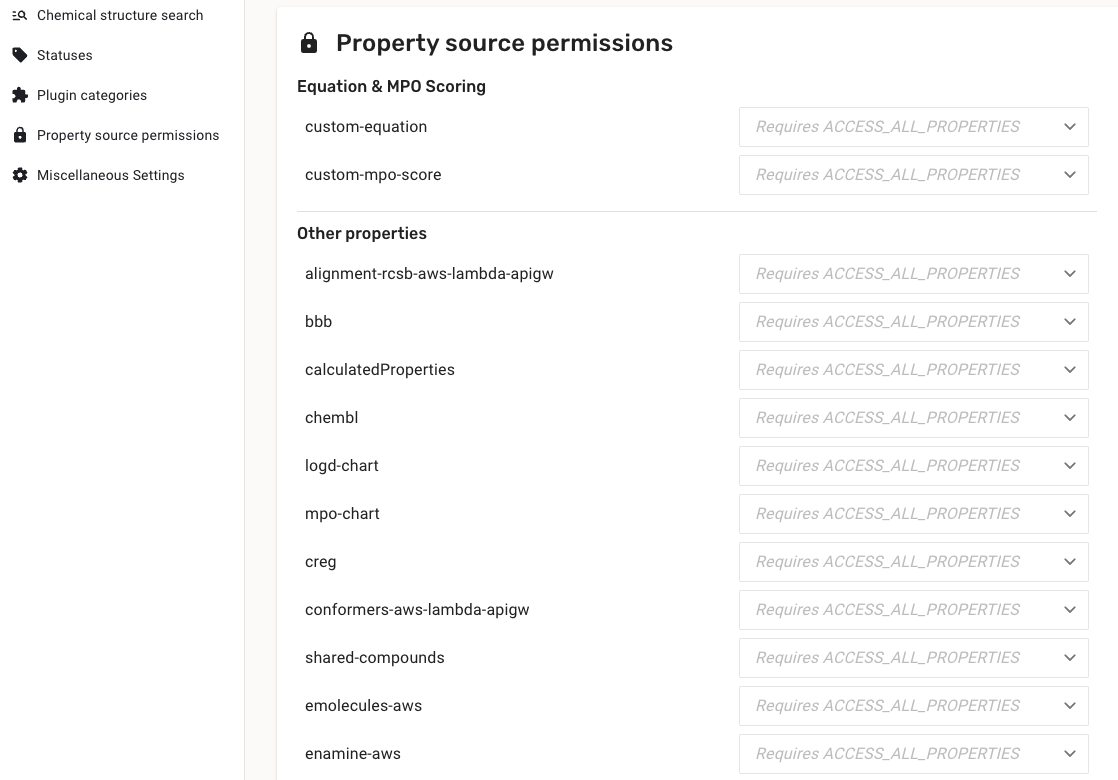
Realtime plugins are organized into Plugin categories, which can be managed under the ‘Plugin categories’ section of the admin interface. Each category contains a configurable list of compound properties.
Every compound property source must be assigned to one of the three ACCESS_PROPERTY_GROUPS under the ‘Property source permissions’ section. This assignment defines which user groups can access which properties.
If no specific group is assigned, the default is ACCESS_ALL_PROPERTY, granting full access to the property and any imported data.
Structure search advanced configuration
Design Hub is using JChem Microservices DB for indexing and searching chemical structures.
By default, the initial structure search maximum hit count is limited (limitStructureSearch) for performance reasons. In case this limit is reached Design Hub tries to refine the search by limiting the results to a subset of the whole dataset (limitFilterToIds) and running the search on the subset again still with a maximum hit count (limitFilteredStructureSearch).
The following settings are available for fine-tuning performance and correctness:
| parameter name | default value | description | available for |
|---|---|---|---|
limitStructureSearch |
10000 | maximum hit count of the 1st search | all search types |
limitFilterToIds |
100000 | maximum number of ids provided for the refined search | substructure only |
limitFilteredStructureSearch |
10000 | maximum hit count of the refined search | substructure only |
structureSearchCacheTTLSeconds |
30 | How long the results are cached for a specific search | all search types |
structureSearchCacheMaxSize |
1000 | How many different search results can be kept in cache | all search types |